Access Management
Overview
The Access Manager module enables administrators to define and enforce access policies for users and applications based on various conditions, including IP address, time range, device, location, VPN usage, and mobile device policies.
This module ensures your organization's data is accessed only under trusted and compliant conditions.
Watch Video
Navigation Path
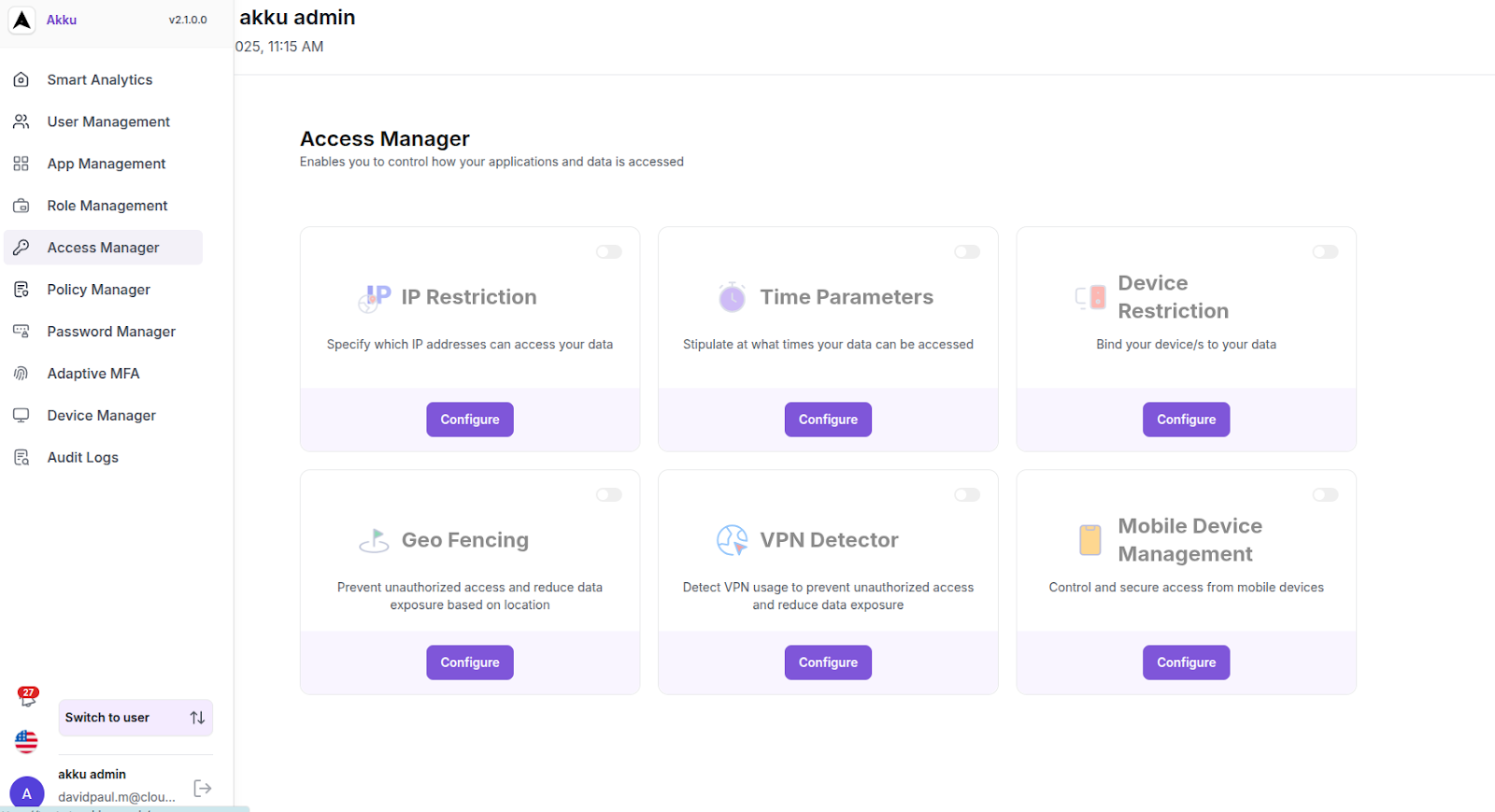
Access Management Features
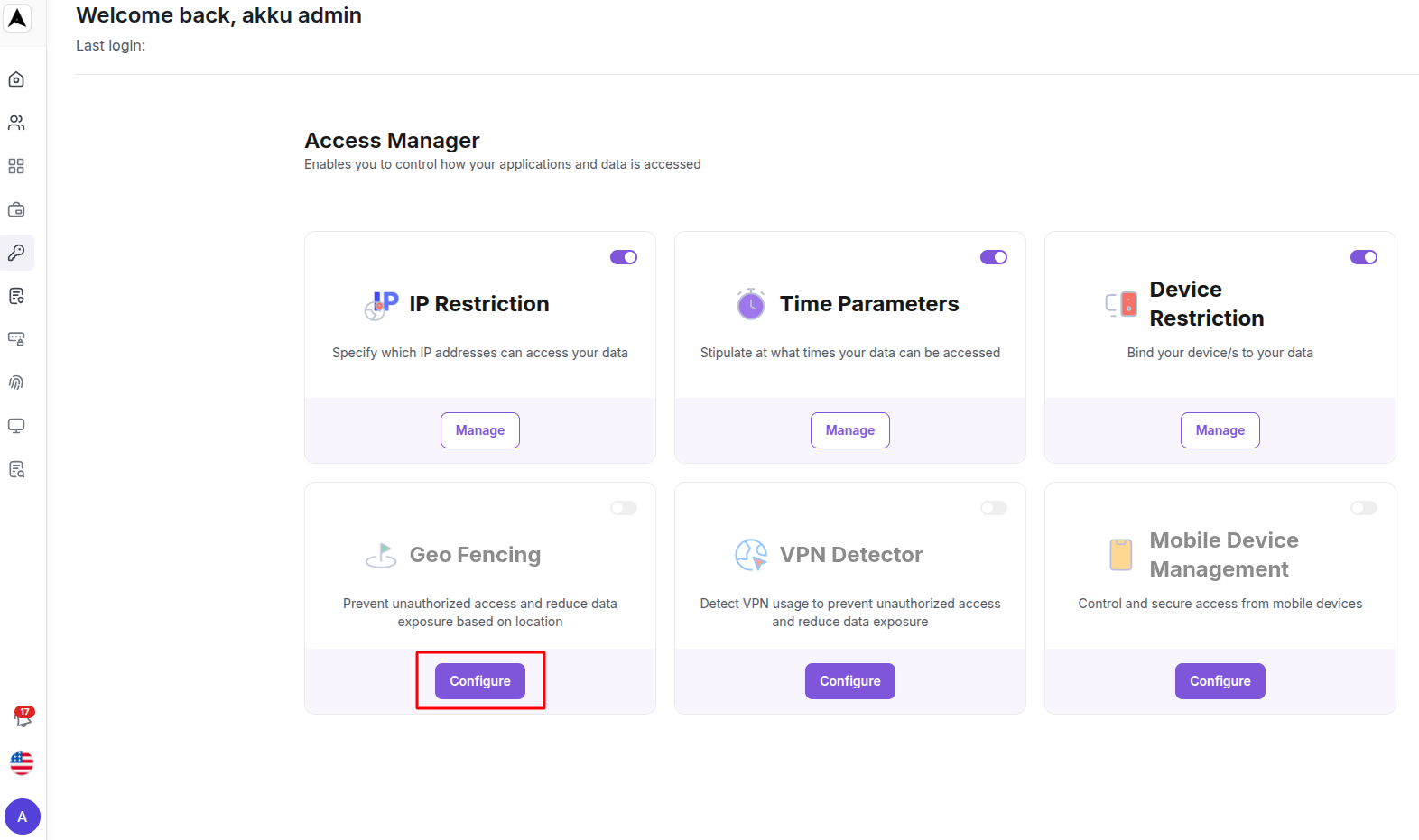
When you land on the Access Manager dashboard, you will see a list of available access rules based on IP Restriction, Time Parameters, Device Restriction, Geo-Fencing, VPN Detector, and Mobile Device Management.
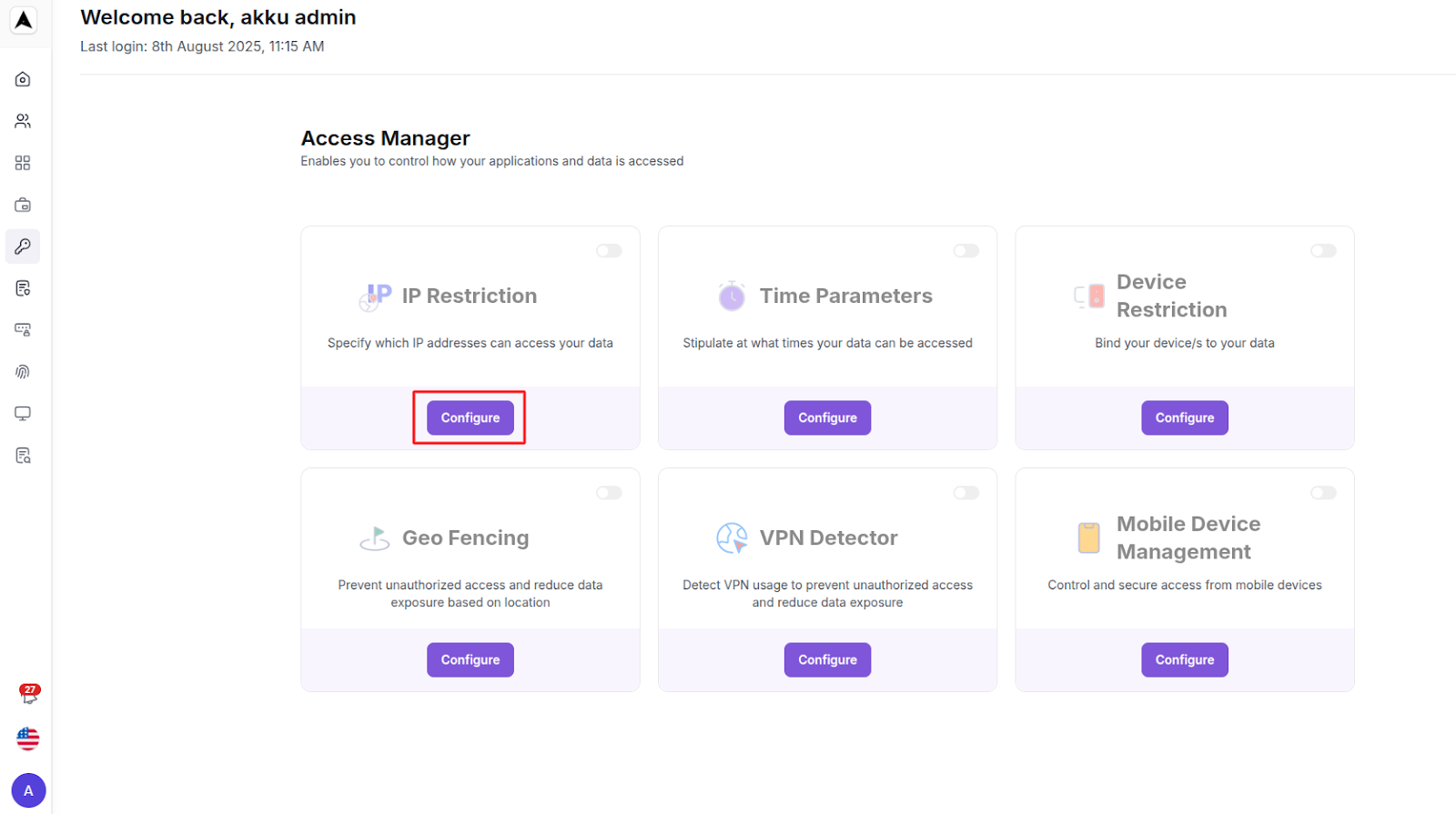
IP Restriction
Specify which IP addresses can access your data
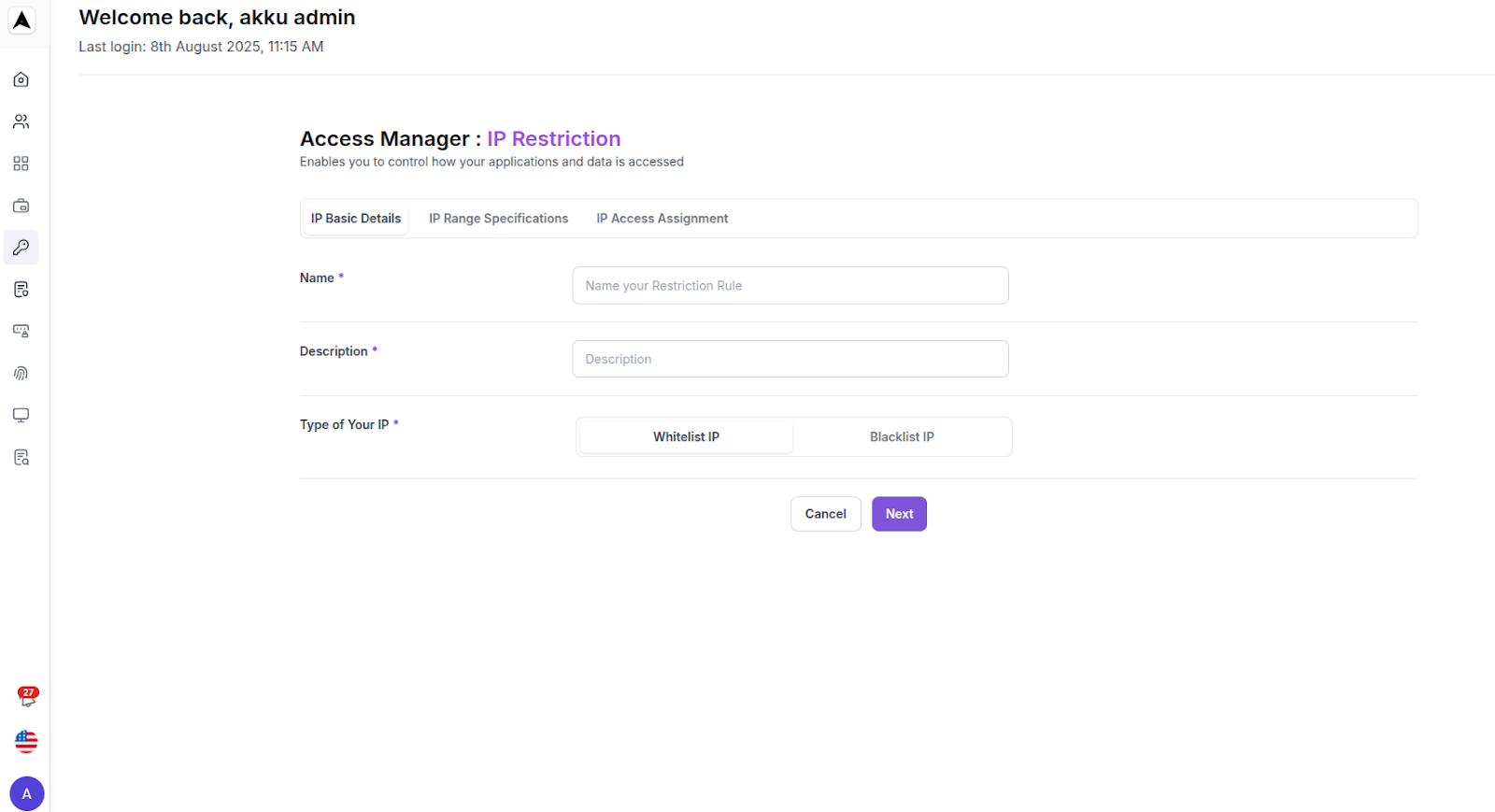
Enter IP Basic Details
| Policy Field | Configuration Details |
|---|---|
| Name | Enter a unique name for the IP policy |
| Description | Enter a brief description of the policy |
| Choose type for IP | Select from the options below: Whitelist IP - Allow access only from these IPs Blacklist IP - Deny access from these IPs |

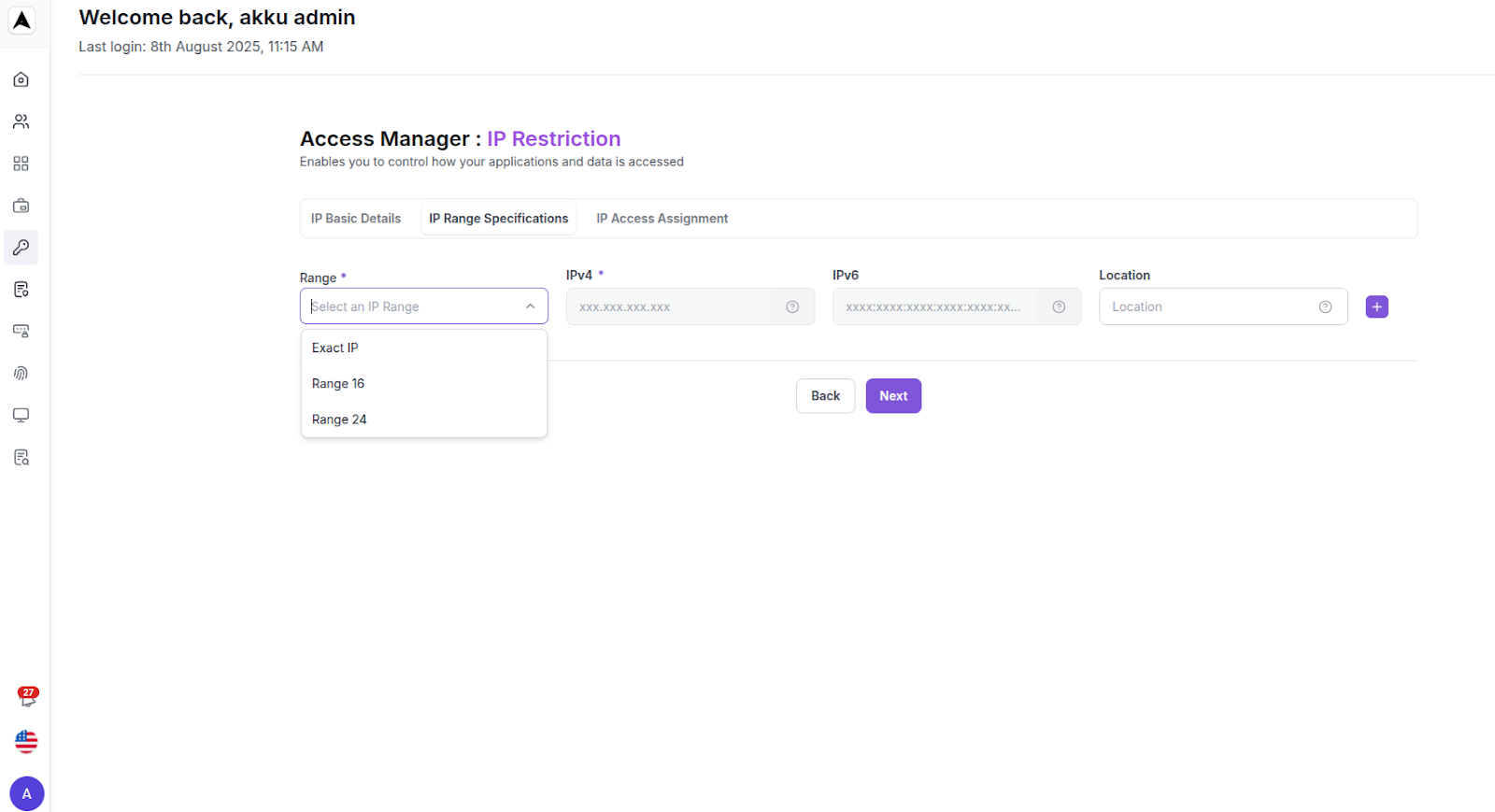
IP Range Specification
| Network Parameter | Configuration Guide |
|---|---|
| Range | Define IP ranges |
| IPv4 / IPv6 | Enter the IPv4 or IPv6 details - both are supported |
| Location | Enter the location tag (optional) |
| Assign to | Assign the rule to the organization, to groups, or to users |
Use the (+) or (-) buttons to Add or Remove in case of multiple entries
Click “Next” to set up the IP-based access restriction assign to Organization or Group or Users.
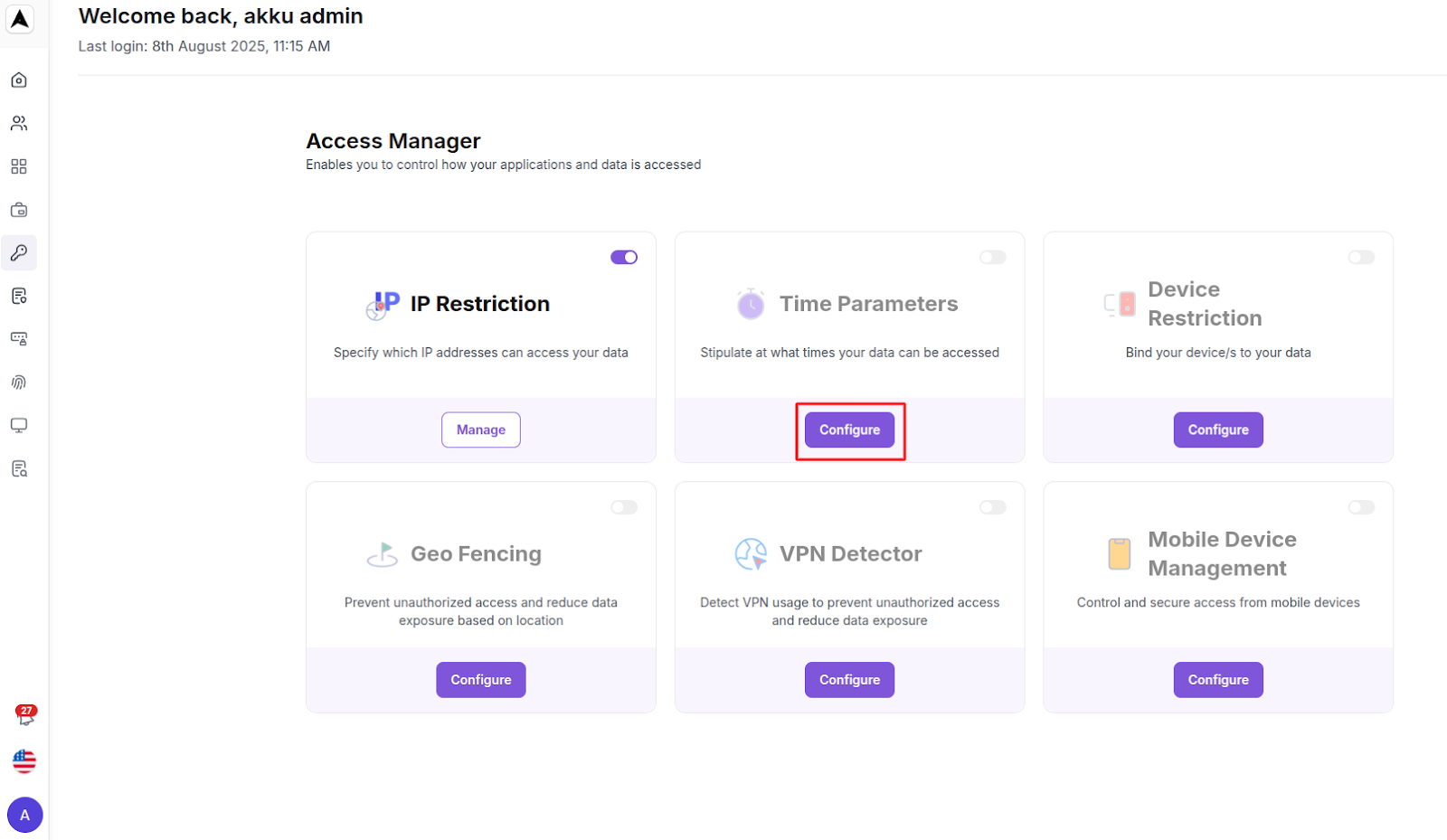
Time Parameters
Stipulate at what times your data can be accessed
Enter Time Parameters details
| Time Rule Field | Configuration Guide |
|---|---|
| Name | Enter the name of the time rule |
| Description | Enter a description (optional) |
| Select Zone | Select the time zone |
| Select Range | Select the start and end time |
| Assign to | Assign the rule to the organization, to groups, or to users |
Use the (+) button to include multiple time ranges.
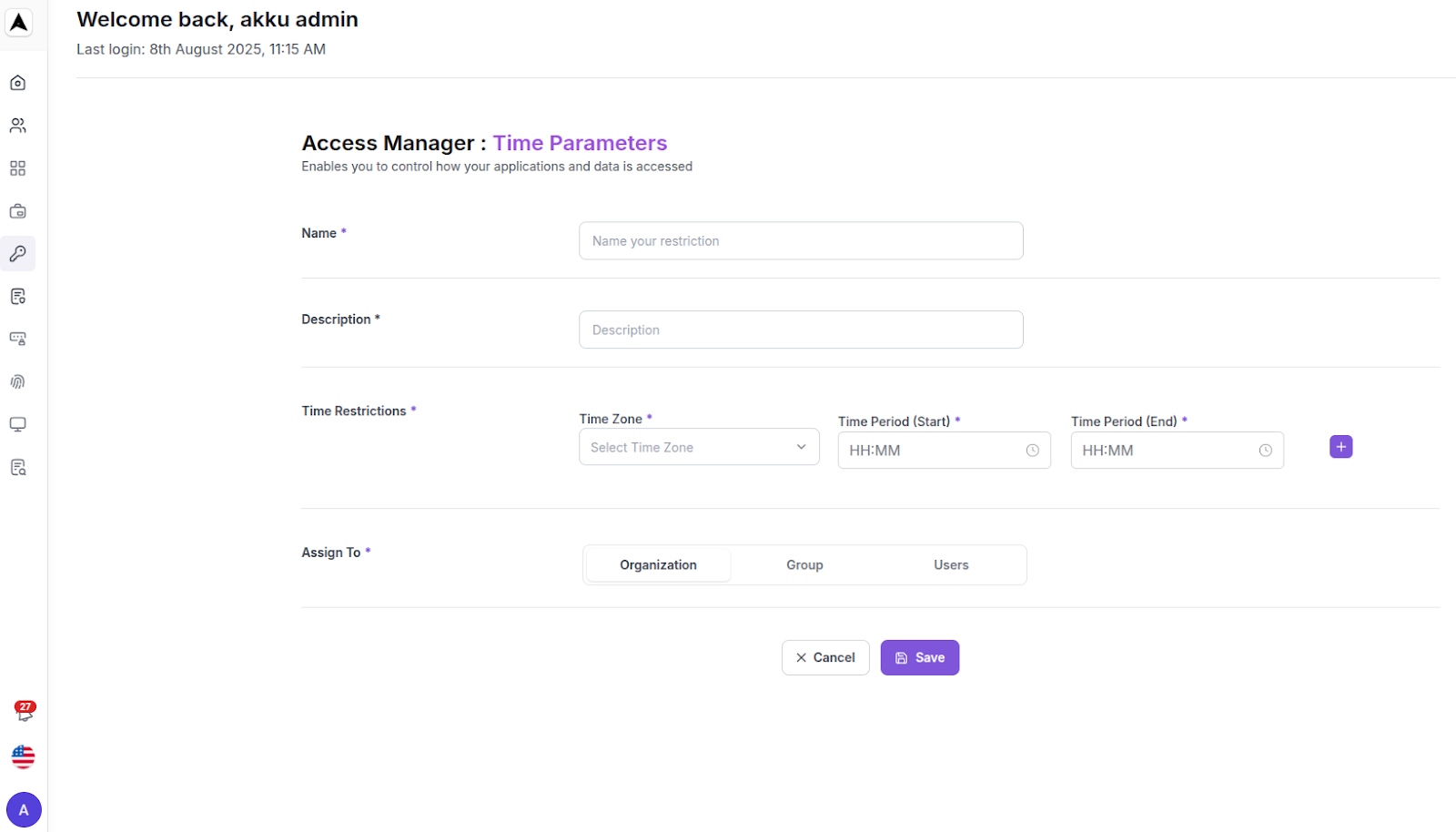
Click “Save” to set up the Time Parameter-based access restriction.
Device Restrictions
Bind your devices to your data
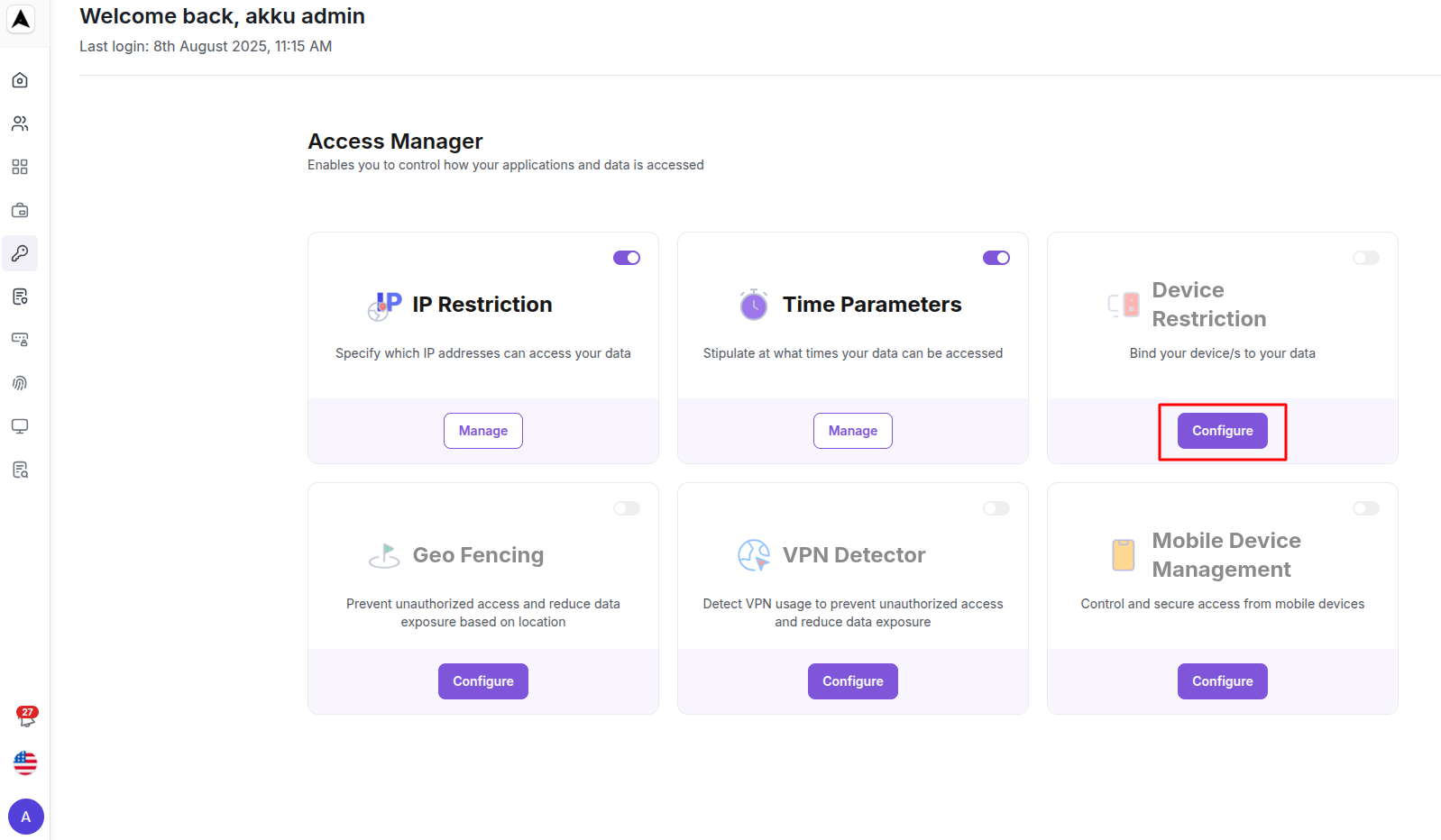
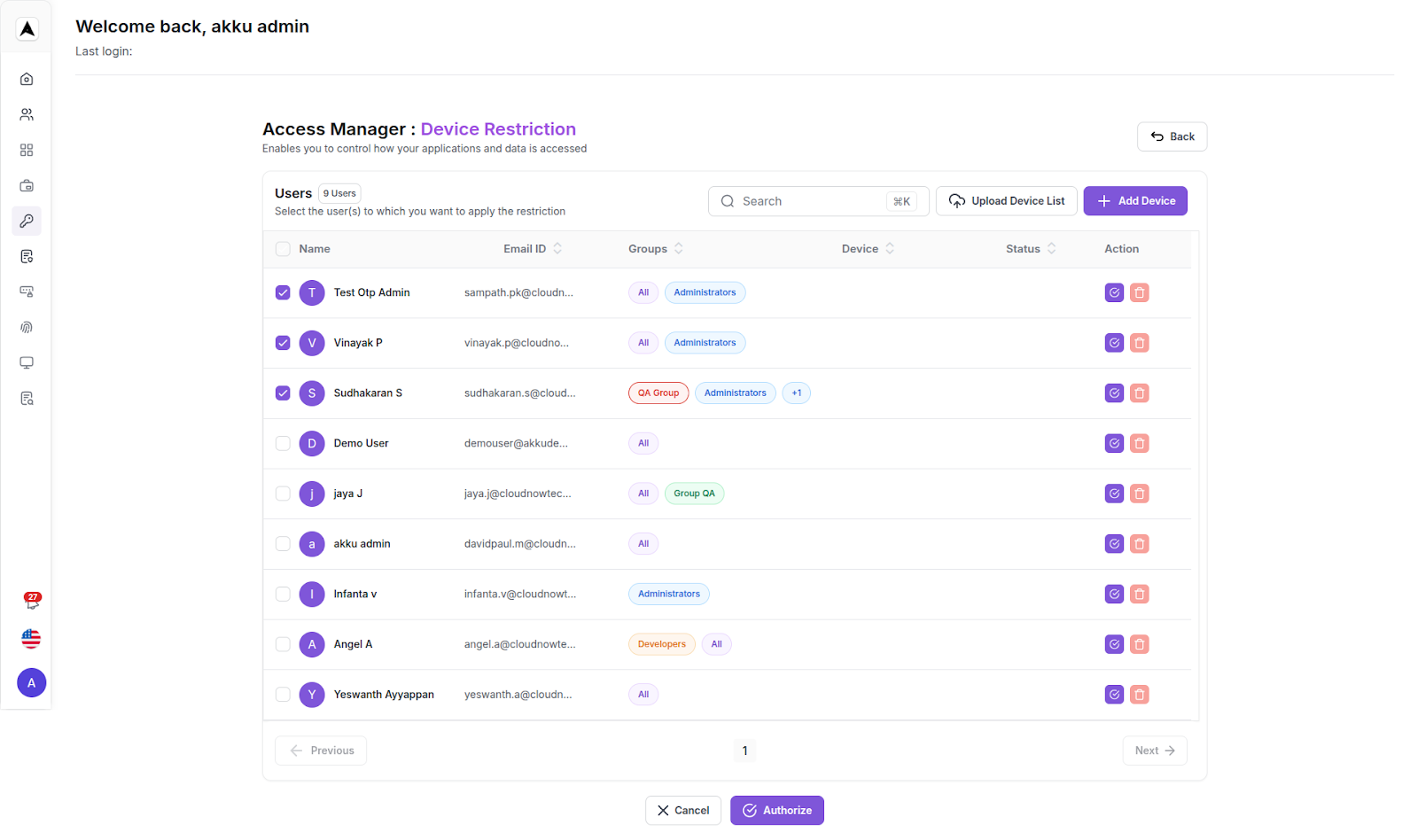
User Selection
A table of all users is displayed with:
| User Attribute | Description |
|---|---|
| Name | Name of the User |
| Email of the User | |
| Device Authorization Status | Authorize the user |
You can:
- Search by User
- Select a User
- Click Authorize to whitelist a device, or Cancel or Exit
Click on the “Send Instruction” button to proceed
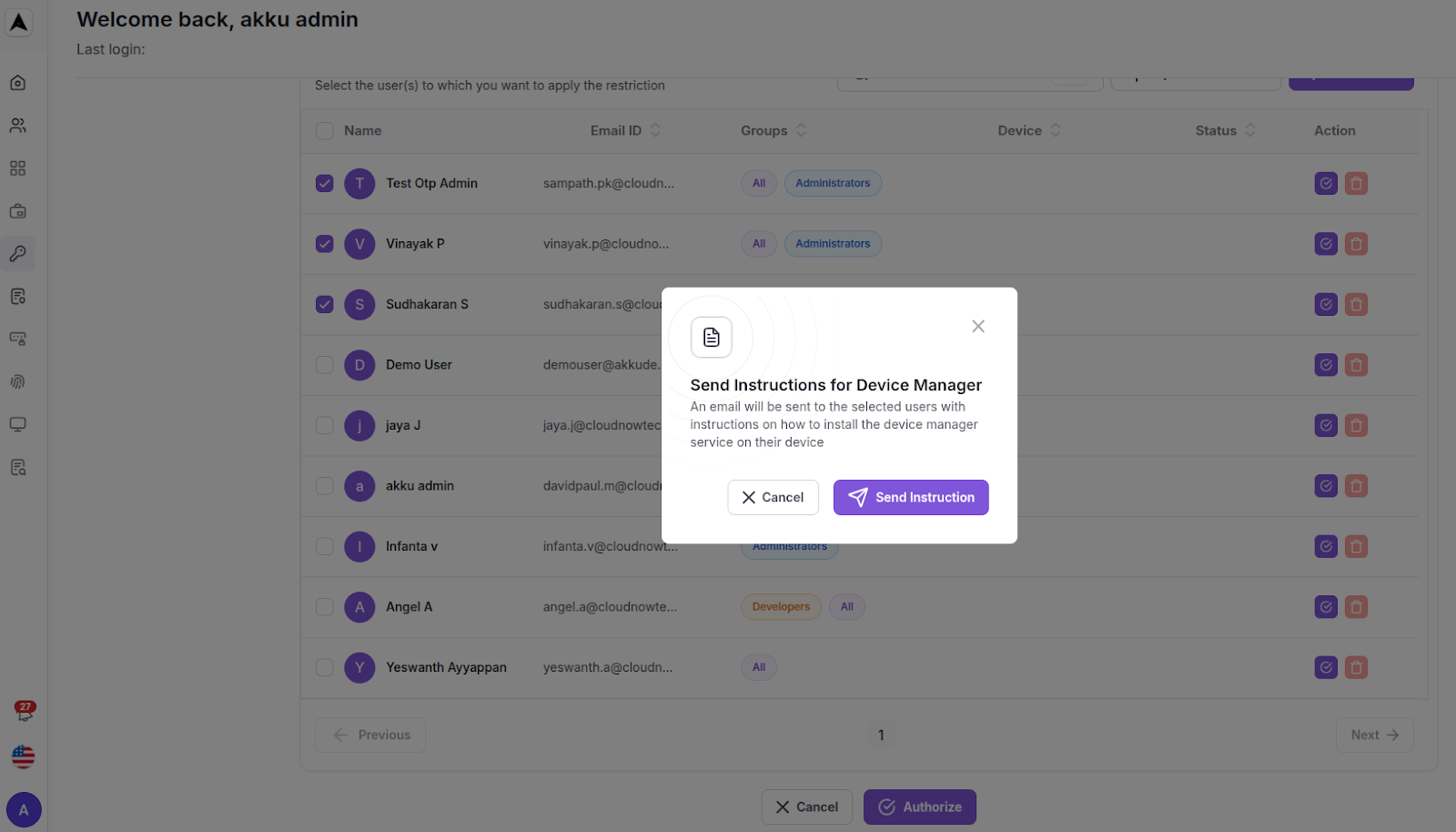
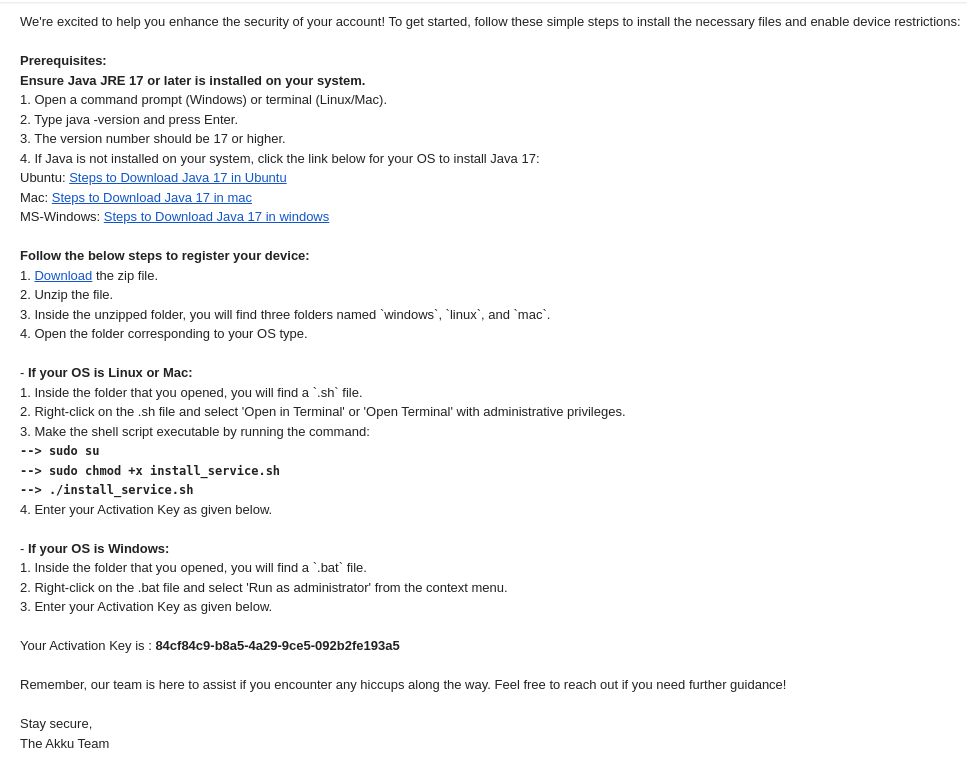
A Screenshot of the email is shown below
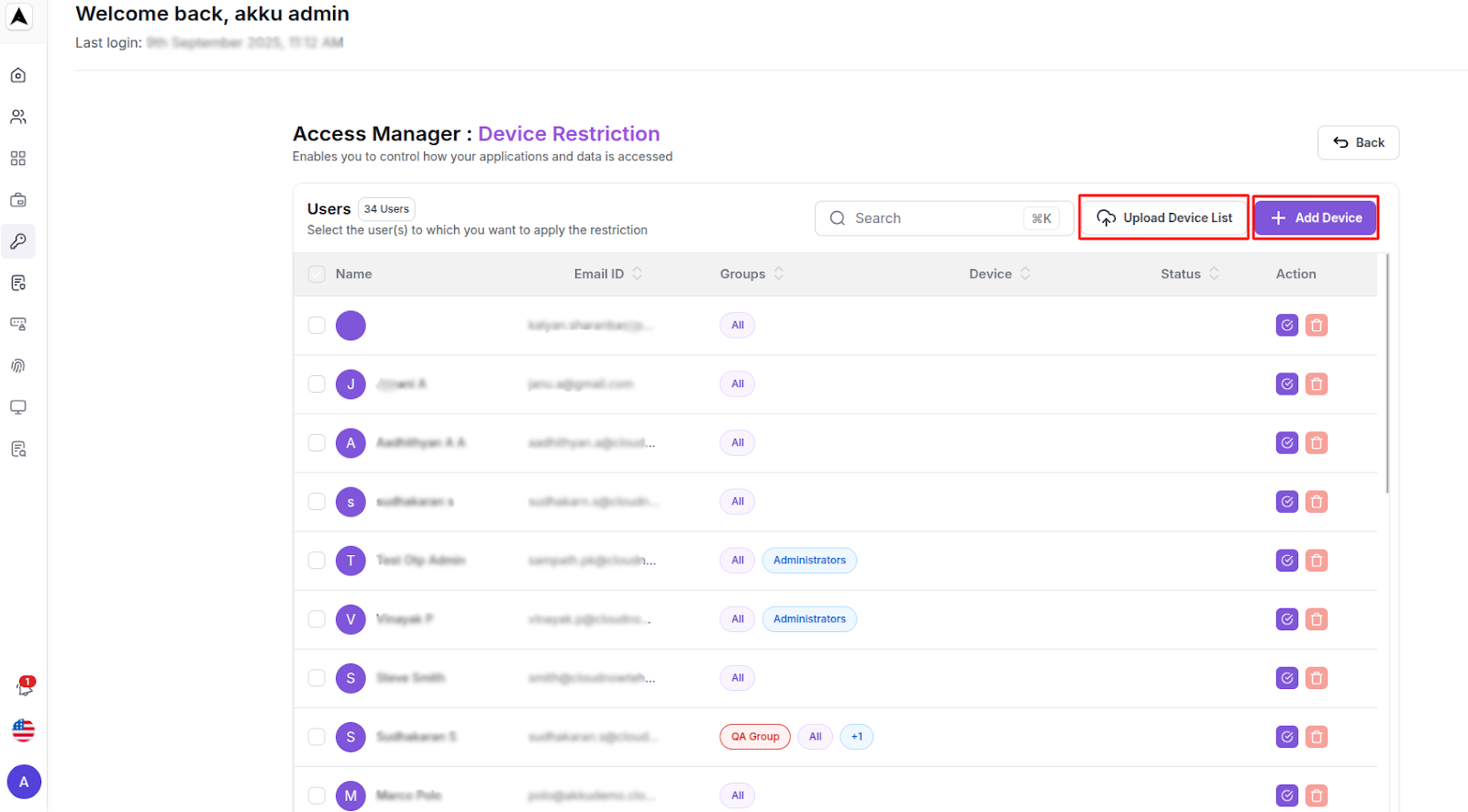
Device Configuration
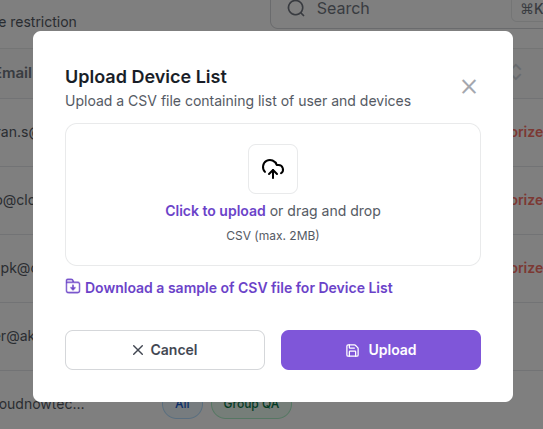
Upload Device List: An administrator uploads a CSV file containing a list of device details (serial number, UUID, type) and their assigned users to add multiple devices at once.
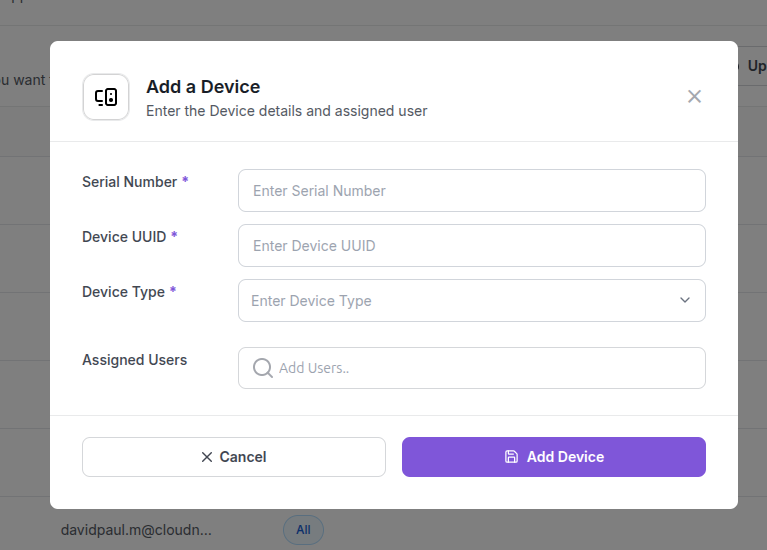
Add Device: An administrator manually enters the serial number, UUID, device type, and assigned user(s) into a form to add a single device to the system.
Geo-Fencing
Prevent unauthorized access and reduce data exposure based on location
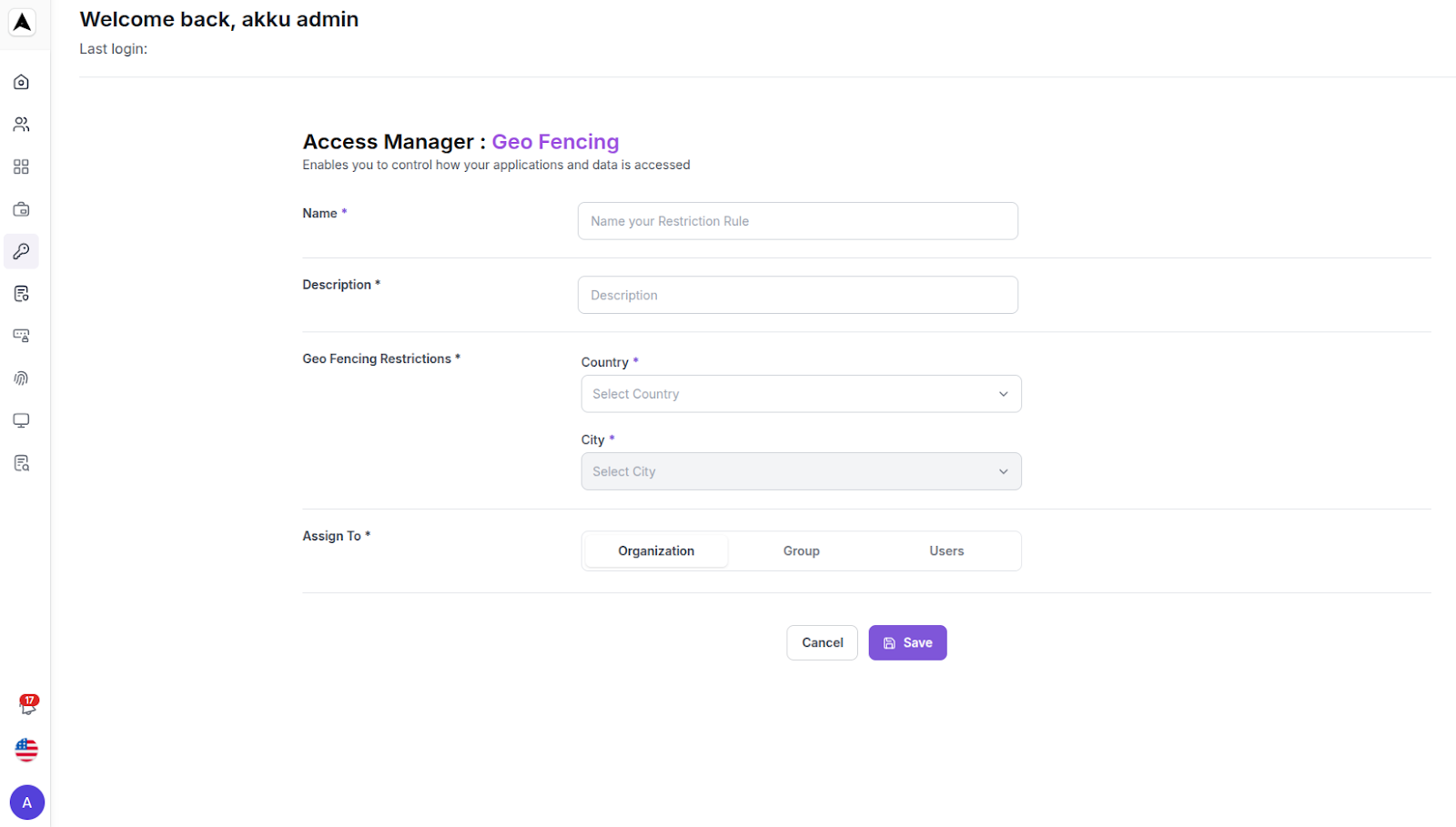
Enter Geo Location rule details
| Geolocation Field | Configuration Guide |
|---|---|
| Name | Enter the name of the geolocation rule |
| Country | Select a country from the dropdown |
| City | Select a city (based on the selected country) |
| Assign to | Assign the rule to the organization, to groups, or to users |
A map interface is also included on the right for visual geolocation selection
Click “Save” to set up the Geo Location-based access restriction
VPN Detector
Detect VPN usage to prevent unauthorized access and reduce data exposure
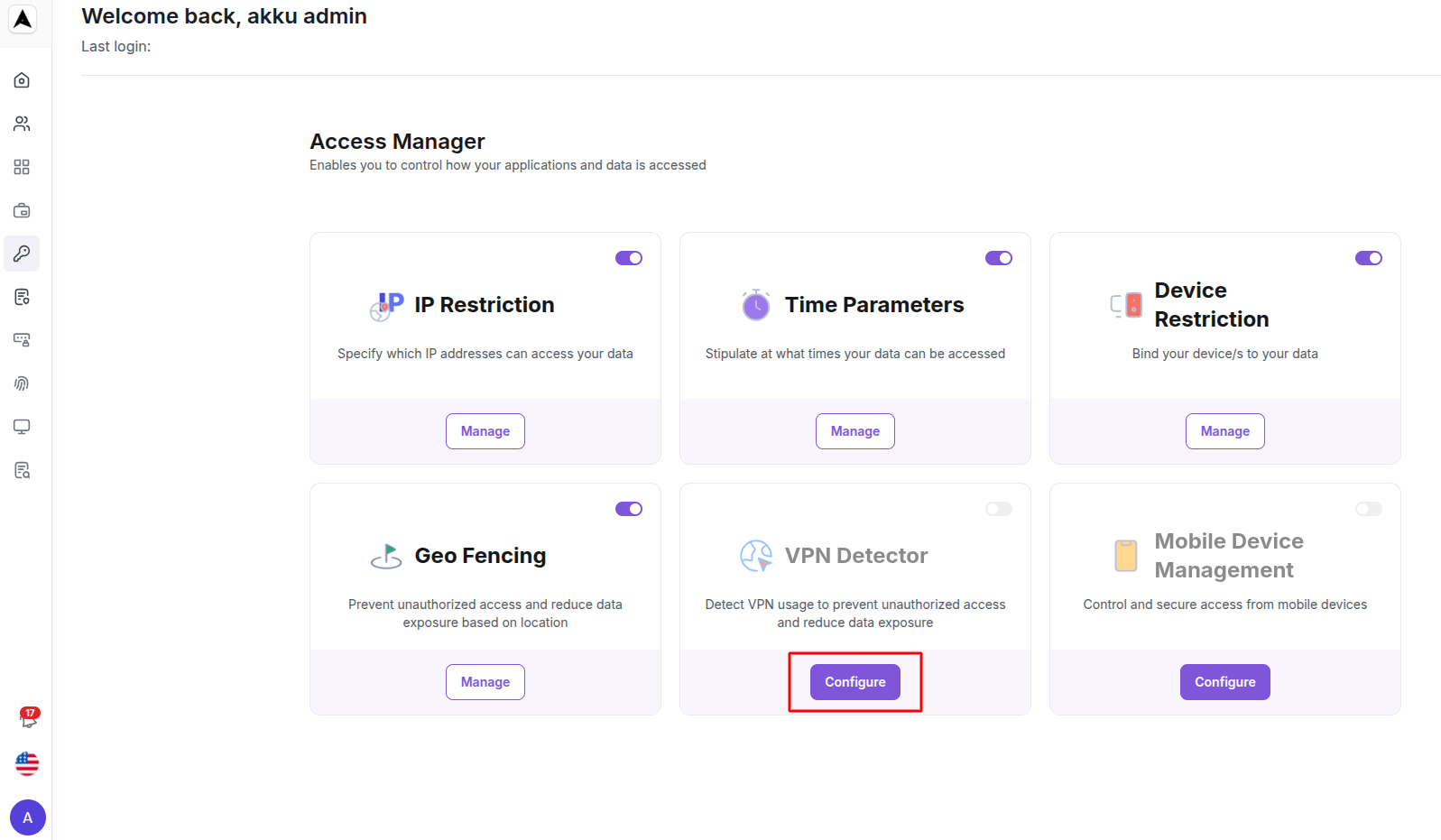
Enter VPN Detector rule details
| Rule Field | Configuration Details |
|---|---|
| Name | Enter the name of the rule |
| Description | Enter a description (optional) |
| Assign to | Assign the rule to the organization, to groups, or to users |
Click “Save” to set up the VPN Detector-based access restriction
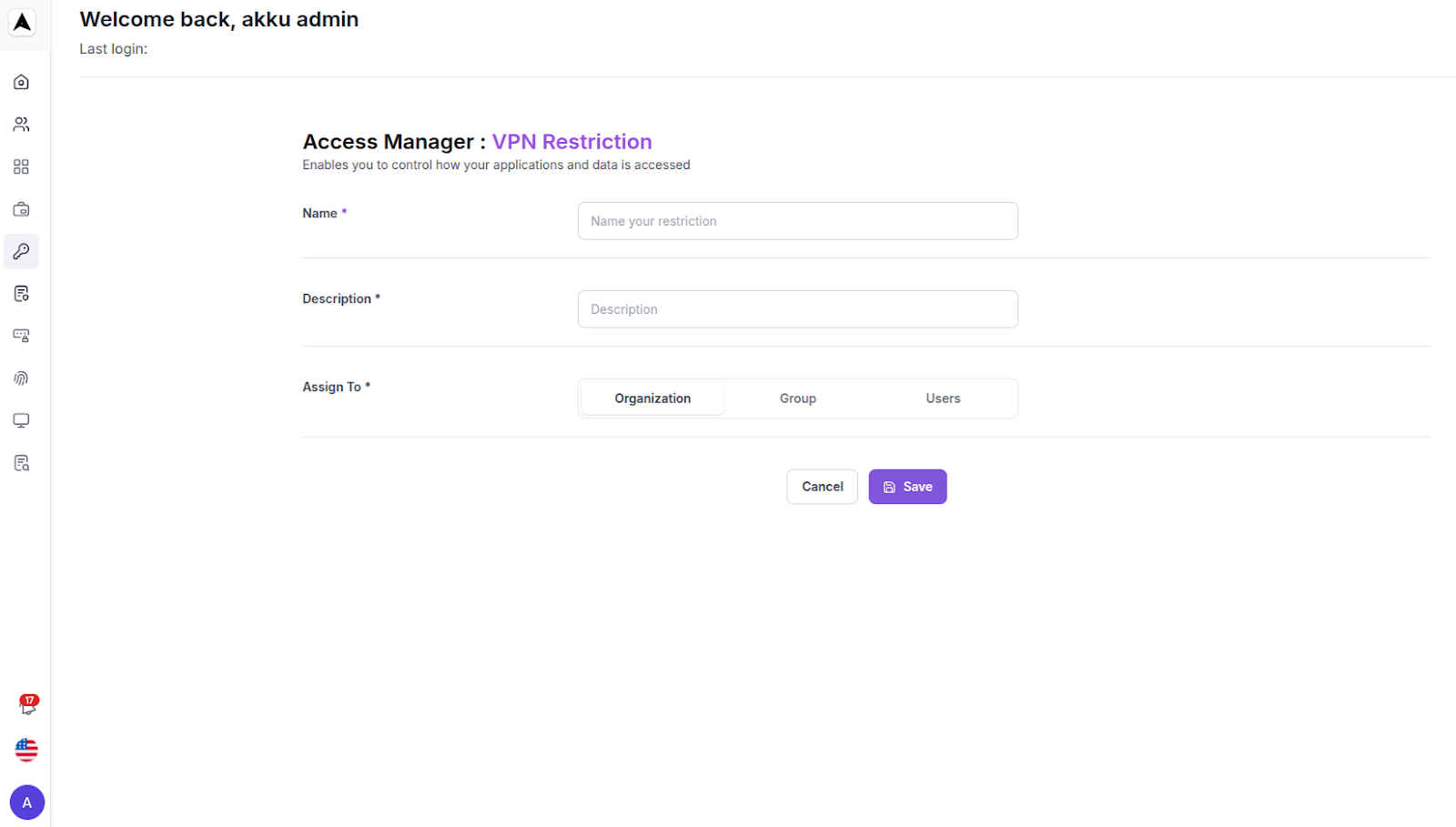
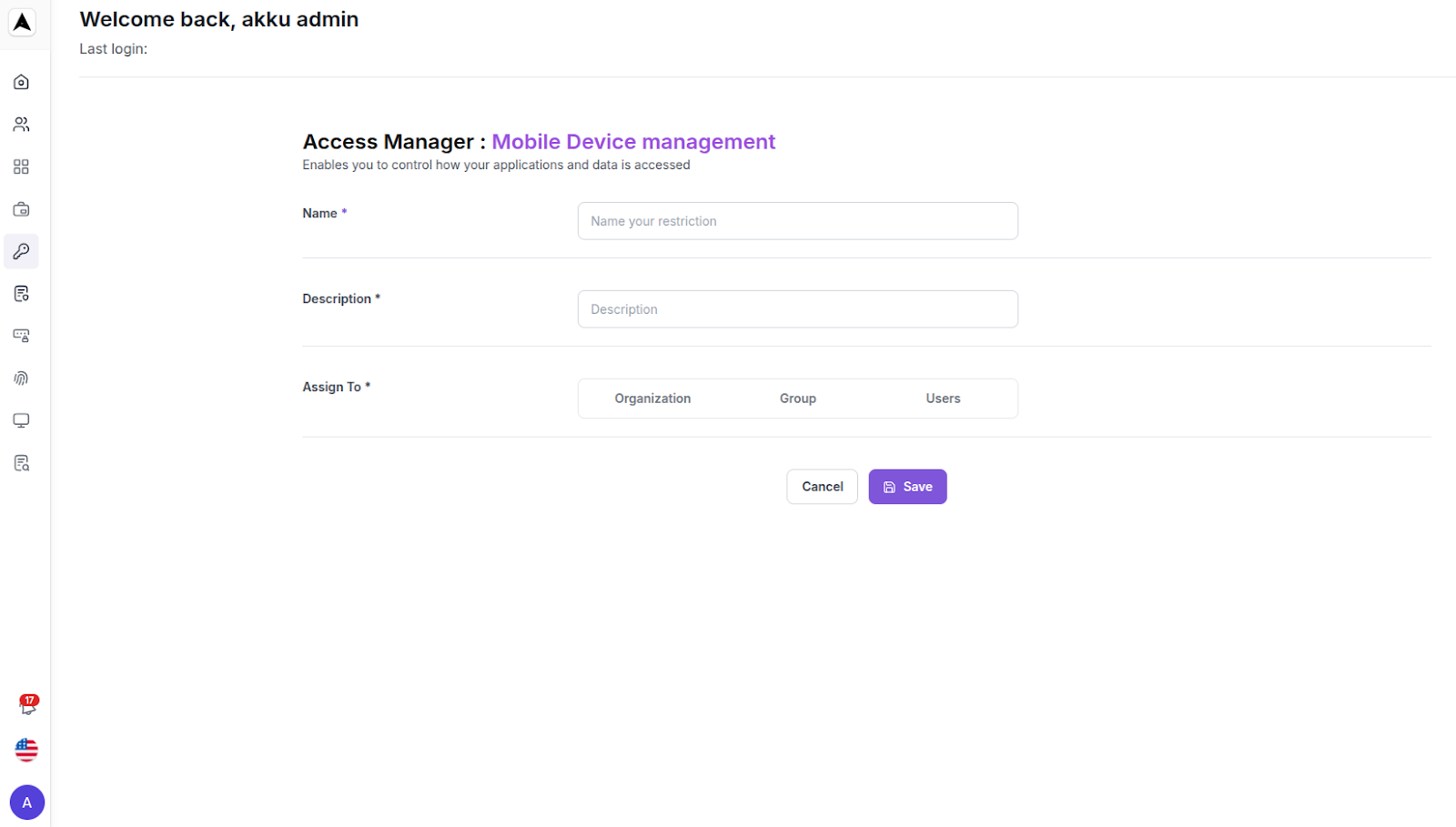
Mobile Device Management (MDM)
Control and secure access from mobile devices.
Enter Mobile Device Management rule details
| Field | Instruction |
|---|---|
| Name | Enter the name of the rule |
| Description | Enter a description (optional) |
| Assign to | Assign the rule to the organization, to groups, or to users |
Click “Save” to set up the Mobile Device Management-based access restriction
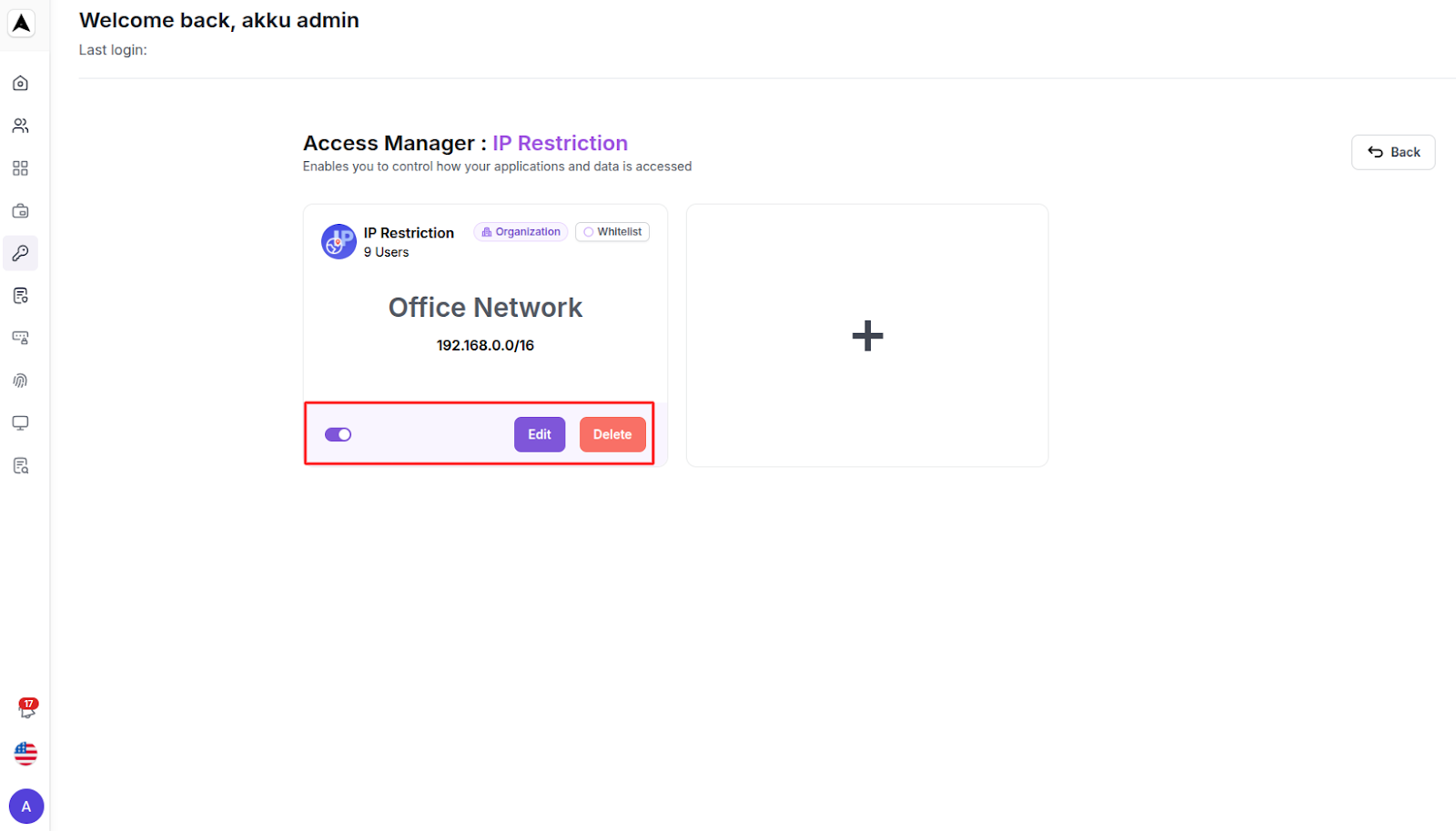
Edit or Delete Access Rules
We can easily edit or delete the access rules by clicking manage on the particular restriction
- Each rule can be edited or deleted using the options alongside it.
- Toggle the Status switch to activate or deactivate an access restriction.
- Click on the Delete icon under Action to delete an access restriction.
- We can do the necessary steps for each restriction as follows if we want.